
Shop Safely This Holiday Season: Cyber Protection Tips for Online Shopping
You don’t need to be a cybersecurity expert to shop safely. Holidays are a time for joy—and online shopping sprees. But with increased shopping comes a higher risk of cyber threats. This guide will show you how to stay safe while hunting for the best deals online.

AI Technologies to Enhance Cyber Defense Capabilities: What you Should Know About Them
Collaboration between human experts and AI systems is vital for effective cybersecurity. While AI handles data-heavy tasks, human intuition and expertise will remain indispensable. This harmonious collaboration will define the future of cyber defense.

The Rise of "Pig-Butchering" Scams: Understanding and Preventing a New Threat in 2024
Pig-butchering scams are not just emerging; they’re surging. These sophisticated scams have ensnared countless victims, tricking them into complex webs of deceit and financial loss. Understanding these scams is crucial in protecting both individuals and communities.

Cyber-Attacks in the Financial Sector: A Rising Threat to Global Stability
As financial institutions become increasingly digital, they attract a breed of cyber criminals whose methods are as diverse as they are dangerous. This escalating threat directly challenges global financial stability, necessitating immediate attention and robust countermeasures.
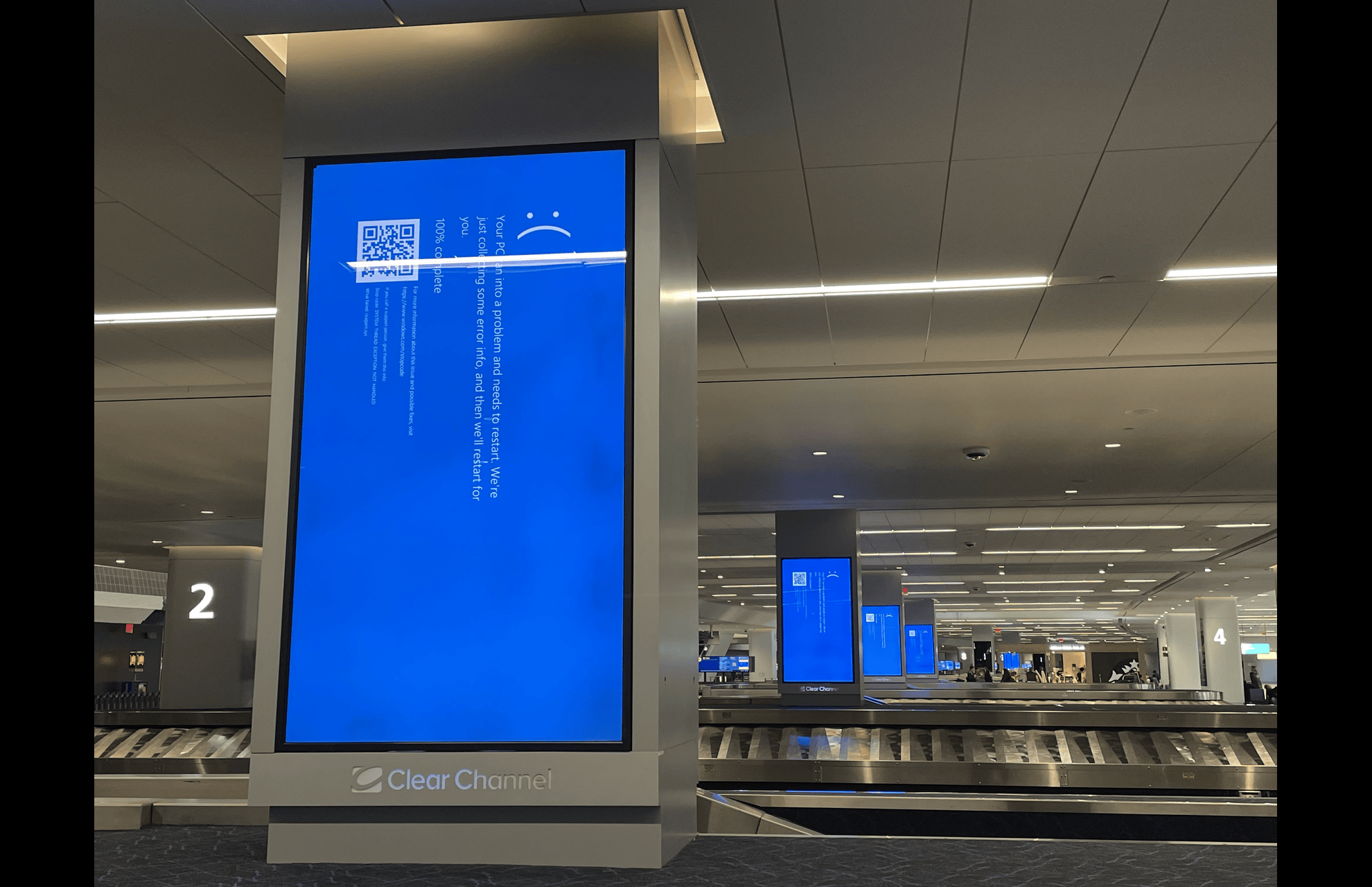
Lessons from IT Outage on Cyber-Resilience for Companies
In recent years, the frequency and scale of IT outages have heightened the urgency for companies to strengthen their cyber-resilience. These incidents can cripple business operations, tarnish reputations, and lead to significant financial losses.

Zombie Computers Phenomenon: A Cybersecurity Nightmare
Not a relic from a horror movie, a zombie computer is a device that has been hijacked by cybercriminals and is operating under their control, often without the owner's knowledge. As threats in cybersecurity evolve, understanding zombie computers and their impact is crucial to safeguard digital environments.
